
From a Guessing Game to Real Data: How 3D Modeling, Digital Twins and Probabilistic Modeling Can Bring Clarity to Security Strategies
Securing a physical utility location takes a lot of work and a lot of imagination. Often, a strategy employed is to “think like your adversaries.” Where would they set up to shoot at a substation? Where would they most likely park their vehicle? What entry points would they consider the most advantageous to accomplishing their nefarious deeds?
Utility security professionals are in a constant battle against the creativity and ingenuity of bad actors. The question is: Is it possible to see every weakness of a site through the imagined viewpoint of an adversary?
Luckily, technology offers a solution to remove the guesswork from this process. Utilities are leveraging digital twins and 3D models to provide data-driven analysis that can help them better prioritize and protect their assets.
By using aerial imagery from drone-mounted devices and structure-from-motion techniques, utilities can generate 2D maps and 3D digital twins of critical utility sites. These digital replicas allow security planners to visualize, simulate and quantify vulnerabilities before real-world events expose them.
This approach allows stakeholders to make high-confidence decisions about where to place cameras, barriers, lighting and other protective systems based on the most likely paths of attack — not gut instinct.
Here are three ways this technology is being used to better identify and map out vulnerabilities:
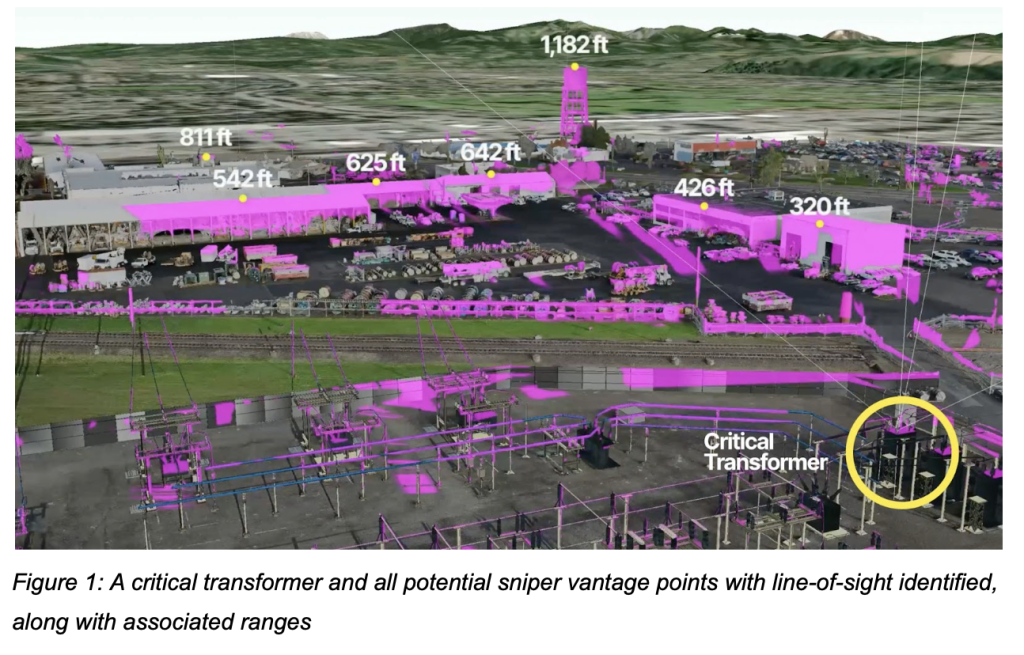
1. Ballistic Line-of-Sight Analysis
Using accurate 3D site models, utilities identify potential attack vantage points to determine which critical assets are visible from nearby roads, fences, hills or adjacent buildings. These analyses are used to inform the placement of ballistic-rated barriers or vegetation berms to block clear shot lines. These tools allow security professionals to tangibly quantify the exact level of risk reduction that ballistic barriers provide.
For example, in the image below, you can see that several building tops and a water tower could be potential substation shooter locations. By seeing the data from those locations, a utility can adjust the placement of ballistic barriers to guard against those vulnerabilities.
2. Security Device Layout Optimization
With digital twins, utilities can virtually test different configurations of security devices, such as pan-tilt-zoom (PTZ) cameras, infrared sensors or lighting fixtures. This can simulate the viewshed and coverage of each camera and overlay that data onto the site model. This approach reimagines the current outdated method of placing devices by relying on blueprints or Google Earth screenshots.
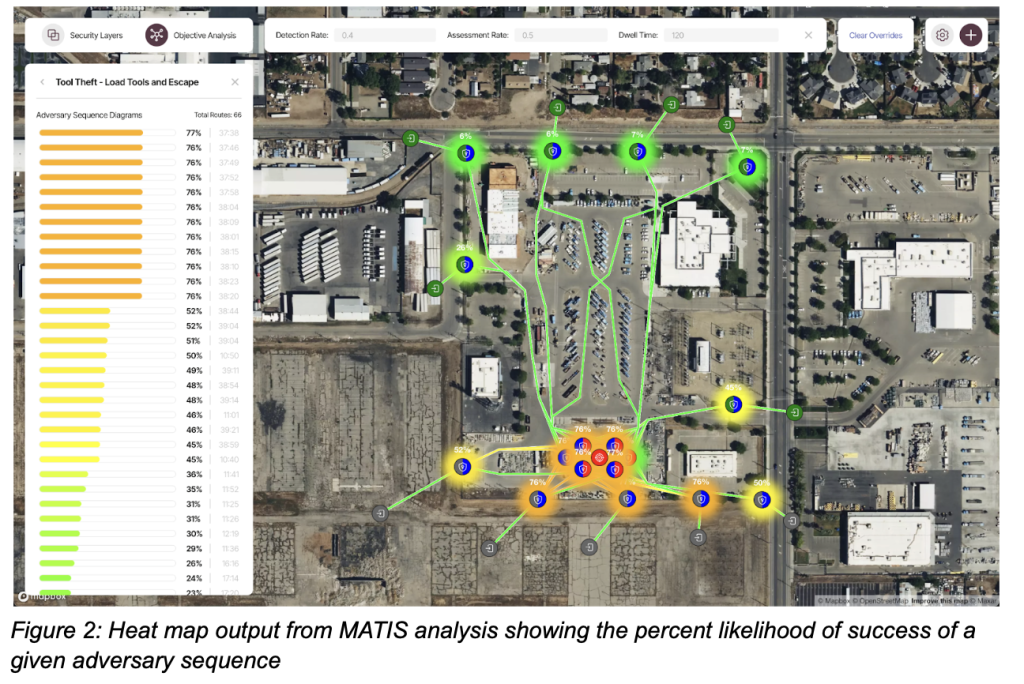
3. Adversary Sequence Diagram Analysis
Utilities can use the data gathered to simulate hundreds — if not thousands — of possible adversary sequence diagrams through a facility. Each path considers detection and assessment probability, aggressor dwell time and transit time between site features. A good solution will generate a risk-weighted map of the most likely infiltration routes and identify weak links in the response chain. For utilities with limited capital, this provides a way to quantify which interventions — such as reinforcing a breach-prone fence or increasing detection probability — offer the best return on investment.
From Data to Dollars
Utilities are not short on technology. What they often lack is clarity — an integrated, data-driven picture of where their next dollar should go and how to justify that to all relevant stakeholders.
Utilities don’t just need better security; they need defensible spending plans. These types of modeling tools make it possible to answer questions such as:
- Which critical assets are most exposed to line-of-sight threats?
- How much of our risk is reduced if we install these ballistic-rated barriers?
- What is the most likely path for a bad actor that we haven’t accounted for?
- What’s the impact on response time if we relocate a camera or increase lighting?
The future of utility security lies at the intersection of geospatial intelligence and probabilistic modeling. By pairing 3D digital twins with simulation tools, utilities can move from a reactive posture to a proactive strategy.
This is not just about maps or models — it’s about decision clarity. When stakeholders can understand vulnerabilities and the quantifiable impact of mitigation options, they gain confidence in their investments and credibility with regulators, auditors and the public.
Better visibility leads to better security. And for the utility sector, better security means safer communities, more resilient infrastructure and smarter spending.
—————
About Dr. Mike Yeager
Dr. Mike Yeager is the co-founder of Solstrata, a security technology company that equips utilities with digital twins and advanced threat modeling tools to defend critical infrastructure. He holds a doctorate in structural engineering, where his research focused on developing cutting-edge software for the U.S. Navy in the field of structural health monitoring. Today, Yeager leads the development of MATIS (Markov-chain Analysis for Threat Infiltration Scenarios), a simulation platform used by major utilities such as PG&E to assess vulnerabilities and design smarter security strategies. His work bridges national defense research and real-world infrastructure protection.