
Lessons Learned from the Brian Thompson Assassination
VRP Group’s COO Ross Falisi Details Why Executives Should Consider this Event an Eye Opener and What it Takes to Adequately Protect High Profile Utility Personnel
CURTIS MARQUARDT JR: Thanks for joining us, Ross! Can you tell our readers a bit more about yourself and your security background?
ROSS FALISI: Thank you for having me, truly a pleasure being here. I started my career as a police officer in New York City. I spent about four years there and was honored to be selected to the elite NY State Police. I completed the balance of my public service there with a variety of assignments. I was on terminal leave when the 9-11 attacks happened. I, like everyone, grabbed my gear, including my canine, and spent the next few weeks at ground zero…

The Real Bottom-Line Costs of False Alarms
Utility security professionals know it takes a multilayered approach to have effective security. What might not be known is just how multilayered the financial impact of false alarms can be to a utility. We sat down with Yaron Zussman from Magos to talk about the bottom-line costs of false alarms and what your organization can do to ensure they are minimized.
Utility Security: What are the biggest challenges utilities face when it comes to implementing a perimeter security strategy that minimizes false alarms?
Yaron Zussman: One challenge I often see is that organizations might not be conducting a thorough enough risk assessment and survey for each site so that they can get better insights into what technologies best match the need…

Knowing Your Risks and Vulnerabilities and How to Prioritize Budget to Close Gaps
In a moment of serendipity, as I was planning out content for this issue, I took a moment to scroll through LinkedIn when I saw a post by Shawn Wallace that said he and Glenn Engel would be presenting an educational session at GSX. The session topic Wallace posted about has the title “Threats to Critical Infrastructure Sites: How to Evaluate Risk and Prioritize Spend to Close Vulnerabilities.” I immediately thought of how the topics in this session would also be great for this column, especially since this is our GSX-focused issue—and more so because these topics really hit at the heart of the security strategy and the economic realities that demand utility security professionals spend security dollars accurately and efficiently.
Luckily…

Why Your Organization Needs to Conduct Exercises: Understanding the The Bottom-Line Impacts
CURTIS MARQUARDT JR.: Thank you so much for joining us today. Can you please tell our readers more about yourself and your role at the Cybersecurity & Infrastructure Security Agency (CISA)?
GARY BOYER: Absolutely. I’m the Branch Chief for the infrastructure Security Exercise Branch—which is part of the Infrastructure Security Division within CISA. I’ve been in emergency management for about 20 years, the last ten of which I have focused on exercises with the critical infrastructure and private sector communities. We conduct and plan exercises that include seminars, workshops, tabletops and full-scale exercises.
Our team looks to provide cyber security, physical security and convergence, threat vector exercises. For example, with conve…
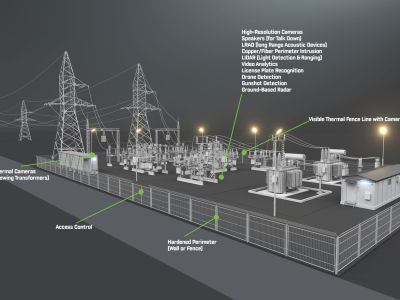
11 Key Questions to Ask Before You Plan Your Security Solution
Can we “Talk Tech”? Leaders are charged with growing profitability, mitigating risks, and improving productivity, but in the utility space reducing threats to infrastructure is also a key deliverable. Although many methods are available to ensure regulatory compliance, the Security Industry Association (SIA) states, “Perimeter security and access control were cited as key components of protecting utilities’ sites, with video surveillance and other technologies playing important supporting roles.” Securing the border, so to speak, is an area where technology can be an indispensable asset.
While hardening any perimeter is paramount, a “layered effect” should be considered in any robust design. Consider early detection options such as short-r…

Are You Prepared for the Next Attack?
Do you believe the energy sector has become a critical watchpoint because of its unprecedented constant attacks? You’re not the only one. More than 700 documented attacks from 2010 to 2020, ranging from cyber to physical to natural hazards, serve as real-life reminders that leaders in the utility space must remain focused on how best to protect our most vital assets, including information technology (IT), operational technology (OT) and SCADA systems for process automation.
Do you recall the horrific physical attack in 2013 on California’s critical infrastructure that exposed the extreme vulnerability of our grid system? A government report leaked to the Wall Street Journal in March 2014 stated, “The U.S. could suffer a coast-to-coast blac…