
Plan Your Path to Security Success: How Strategic, Tactical & Operational Planning are Essential to Creating a Strong Security Posture
President Eisenhower, the five-star general who commanded the largest invasion in history during World War II, stated, “In preparing for battle, I have always found that plans are useless, but planning is essential.”
This philosophy directly relates to utility security for two reasons:
- Establishing a robust security posture is a complex issue that requires planning
- Threats never materialize as planned
In today’s environment, maintaining a strong security posture is essential and effective planning is key to achieving it. However, there are a few obstacles that can hinder the creation of a strong security stance that you’ll need to address. First, recognize that planning is a thankless and time-consuming task that is unappreciated and undervalued by almost everyone, but it is absolutely essential to success. In other words, planning for security is a pain, but it’s important.
Secondly, you need to accept that you face countless threats with limited resources. Essentially, you often have more challenges than available funding to tackle them. Planning helps prioritize which improvements to pursue and provides a solid justification for postponing less critical enhancements when necessary.
Next, realize that the devil is always in the details. Overlooking the minutia creates vulnerabilities, so you have to focus on the smallest details during every part of the planning process. This can be a time-consuming and thankless task, but it’s absolutely necessary. Most security improvement failures can be traced to the lack of detail or a communication gap during the planning process.
But one of the most confounding problems is figuring out where to start. Tackling utility security can be an overwhelming assignment. With the complexity, depth of involvement and demands of enhancing security, determining where to begin is a challenge, but this is where planning begins to pay off.
The ultimate goal of security planning is to protect assets. Effective planning ensures comprehensive protection for all assets, including personnel, information, property, facilities and infrastructure. The aim is to enhance the security posture of the entire organization, with careful consideration given to resilience, flexibility, impact and cost.
The result of effective planning will be a robust, adaptable security strategy that addresses the challenges of threat protection. It will simplify complexity, offer flexibility to tackle unforeseen threats, optimize limited resources and enhance depth to address weaknesses and flaws. Additionally, it will provide a means of identifying and capturing one of the most elusive creatures on Earth: the “starting point.”
Crafting an effective and practical security plan requires a systematic approach. A good strategy is to employ a proven planning model that fits your unique needs. Adopting a tested methodology simplifies the process and enhances defensibility. While many useful methods exist, I personally prefer the Strategic, Tactical and Operational (STO) planning model. The STO model is a three-step process that provides clarity and uniformity and serves as a pragmatic guide for enhancing organizational security posture.
So, just what is STO planning?
In the STO planning model, the terms strategic, operational and tactical denote the key elements of a three-step planning framework. Understanding these concepts is essential for aligning an organization’s goals with its actions and resources.
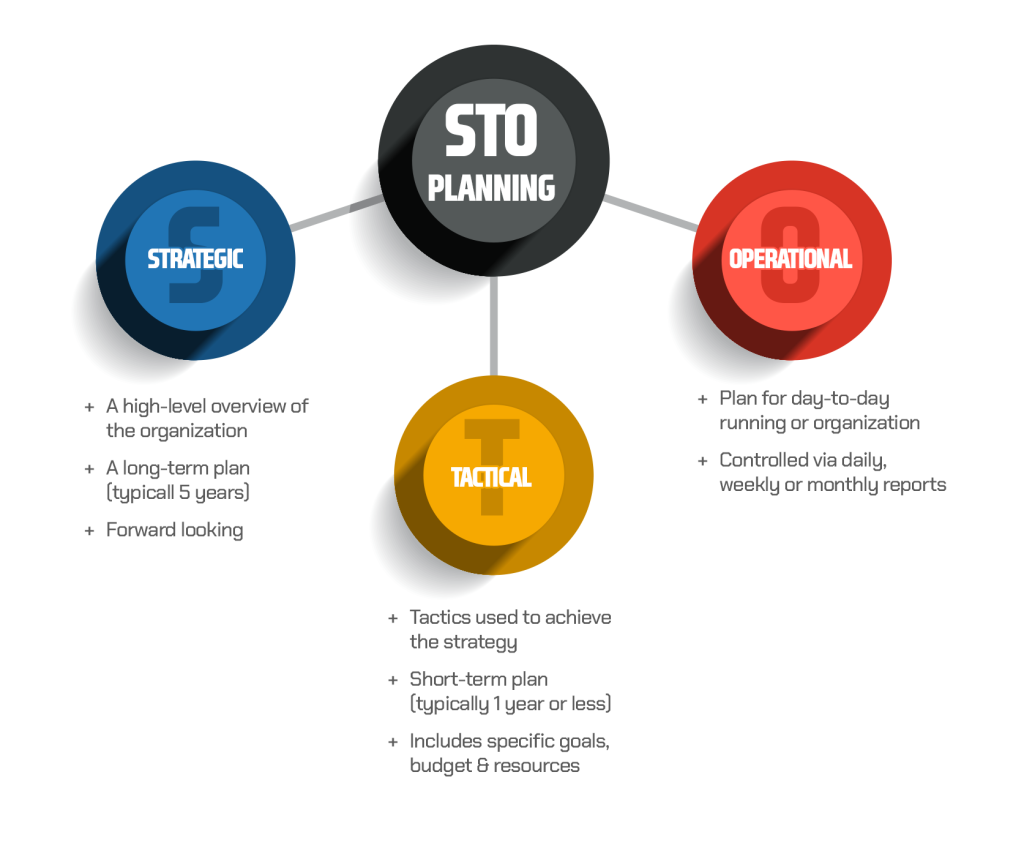
Step One: Strategic Planning
Strategic planning is a high-level decision-making process that establishes the long-term direction for organizational security. It defines the security program’s mission, vision and key objectives. This process involves assessing the organization’s current security posture and determining the optimal security stance that should be achieved and maintained. Additionally, strategic planning includes conducting a threat assessment to identify potential threats and clarify the “who, what, when and where” of asset protection.
Strategic planning outlines the course an organization will follow over several years, usually spanning a five-year period. This type of planning emphasizes long-term goals and objectives. It will also identify key projects, establish benchmarks and determine capital expenditure expectations for security improvements. And, it will necessitate input and guidance from executive leadership and ultimately require approval and support from the CEO and board.
Once approved, the strategic plan serves as the foundation for the security program. Both the tactical plan and the operational plan are developed from the strategic plan. The tactical plan outlines the methods for achieving the goals and objectives specified in the strategic plan, while the operational plan delineates the functional steps needed to implement the security initiatives.
Step Two: Tactical Planning
After completing the strategic planning, the next step is to develop a tactical plan. The tactical plan acts as a bridge between strategic and operational planning. It entails creating specific actions and short-term initiatives aimed at achieving strategic objectives. Tactical plans are more detailed than strategic plans, specifying the steps to be taken, the resources to be allocated and the schedules to be followed to accomplish specific goals.
Tactical plans generally include initiatives that are to be executed over a one- or two-year period. These are actionable documents managed by middle and lower management. Tactical plans ensure that the strategic vision translates into concrete, actionable tasks that can be effectively implemented.
An effective tactical plan will develop a flexible and practical security approach that minimizes the impact of security practices and restrictions on daily functions and operations while providing essential resources and strategies for asset protection.
Once the tactical plan is developed, the specific tasks, projects and initiatives identified are extracted and further detailed in individual action plans. These action plans provide the necessary detail and guidance to implement specific elements of the tactical plan.
Action plans are integral parts of the tactical plan. They specifically address individual elements or groups of related elements within the tactical plan, detailing the specific steps required to achieve the assigned security element, improvement project or initiative.
The ultimate goal of the tactical plan and its associated action plans is to achieve the objectives of the strategic plan. Once these goals are met and the desired security posture is established, operational planning ensures that security remains effective, functional and consistent.
Step Three: Operational Planning
Operational planning addresses the key components of daily security. It transforms strategic goals into actionable tasks, processes and functions. Operational plans leverage the security framework established by tactical planning to develop and implement practices and procedures that are not only effective but also sensible, practical and adaptable.
Operational planning emphasizes efficiency and productivity, ensuring that the organization’s resources are utilized effectively to achieve its strategic objectives. Security staff and middle management are responsible for carrying out the functions of an operational plan, which encompasses the processes, systems and resources necessary to support the organization’s ongoing operations.
A strong operational plan will include flexibility in security practices. This is a vital step for utilities, as rigid security measures can create unnecessary constraints and impede daily utility functions and operations. An effective plan will outline incremental security measures tailored to the current threat environment. For example, a common strategy is to implement a three-level threat condition system.
- Condition Green (Normal/Low threat risk)
- Condition Yellow (Elevated/Increased threat risk)
- Condition Red (High/Severe threat risk)
An operational plan that utilizes a functional threat condition system will help promote consistent adherence to security practices. It achieves this by allowing relaxed yet effective security measures to be implemented most of the time while ensuring that increased security measures are quickly accessible and employed during periods of heightened threat.
To create an operational plan, another planning framework is often used. One of the best options is the PACE planning framework, which is among the most effective models for developing a functional operational plan. The military established PACE to ensure efficient communication during combat operations, so it has been tested under pressure. PACE stands for Primary, Alternate, Contingency and Emergency and it can be highly effective for planning security operations. The PACE framework is a four-step process that requires you to consider not only your primary method for achieving a security objective, but also to explore alternative methods in case your expected approach fails. We will explore the use of the PACE planning framework in an upcoming article.
In conclusion, the STO planning approach is one of many valuable planning models that can be utilized to achieve improved security. However, for me, it has been one of the most effective and easiest methods for developing a functional and attainable security program.
The STO model consists of three steps —
- develop a strategic plan that identifies where you’re going
- make a tactical plan that maps out the route
- build an operational plan that gets you there
The STO planning model is a practical method that anyone can follow. It will identify the most effective way to allocate limited resources, provide the necessary details to ensure success and pinpoint the elusive starting point. As I stated earlier, security planning is a thankless and time-consuming task, but its value is immeasurable and absolutely essential to success.
About Jim Willis:
Jim Willis is president of InDev Tactical, a security training and consulting firm. He is an electrical engineer, an experienced utility professional and a credentialed homeland security specialist and anti-terrorism expert. If you want to discuss utility-focused security training or consulting assistance, you can reach Jim at 703-623-6819 or jim.willis@indevtactical.net.