Will Your Critical Substation Survive an Attack? (Part Four)
Ross Johnson Continues and Closes His Insightful Series on Substation Protection
In the previous three issues, we asked how you would know if your critical substation would survive an attack. (It might be a good idea to go back and re-read the columns: PART 1 | PART 2 | PART 3)
In this issue we will examine how we choose and test upgrades to the physical protection system (PPS).
Upgrades
Our analysis in the previous issue has revealed two problems in the PPS: the video surveillance system (VSS) cannot cover the full fence line adequately because of the overgrown foliage, and the fence does not delay his progress for enough time to allow the police to arrive.
The team decides to re-run the analysis with two changes to the PPS: the foliage is trimmed back from the fence for three yards around the full perimeter, and the fence is replaced with an anti-cut, anti-climb fence rated for 15 minutes of delay.
We now insert the upgrades in the steps where they will have an impact, so the foliage clearing is in Step 2, and the upgraded fencing is in Step 3. Because the fencing is rated to add 15 minutes delay, we increase the Step Time for Step 3 to 900 seconds.
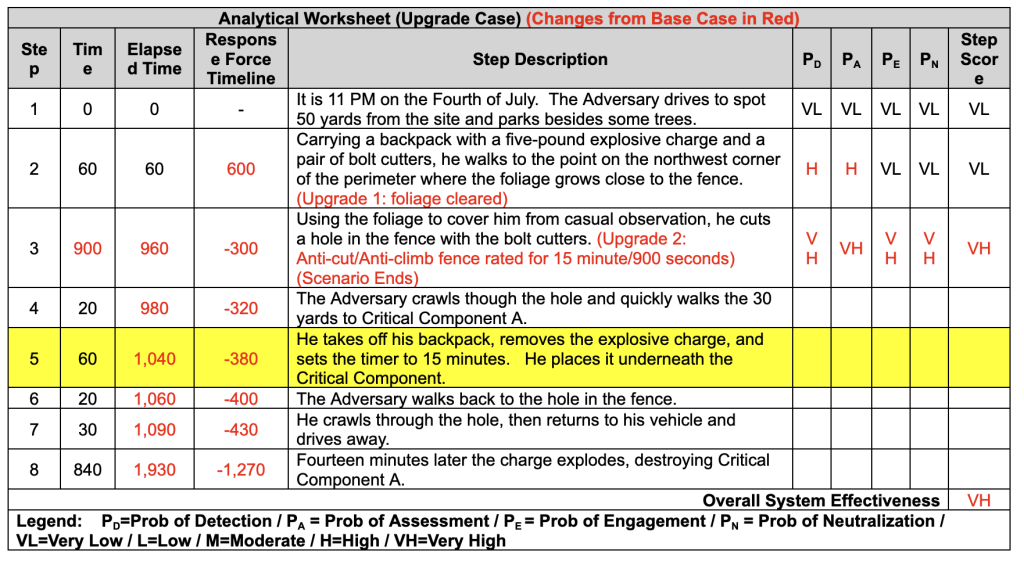
Step 1: No change from Base Case.
Step 2: With the foliage cleared, there is a High probability that the LVM operator will see the Adversary as he approaches the outside of the fence at the place where he plans to cut the hole. Considering the time of night the operator calls the police, and the 600-second response clock starts.
Step 3: It takes the Adversary 900 seconds to cut through the fence, which means that the police arrive 300 seconds before he completes the task. We can reasonably assume that they apprehend the Adversary, and the scenario ends. Because the probabilities of detection, assessment, engagement, and neutralization are all Very High in this step, and as the Step Score is the highest score on the step it also is Very High. As the Overall System Effectiveness (OSE) is the highest of the Step Scores, we can now rate it as Very High.
These upgrades are good for another reason: they keep the Adversary outside of the substation. Although we had assessed that Step 5 was the step that he absolutely has to be stopped before, in reality we should be trying to keep all adversaries out of substations. An intruder armed with explosives or a firearm is best handled outside the perimeter, before they get in amongst energized equipment.
The space available in this column dictates that we have to keep the scenario simple, but it still demonstrates how weaknesses and vulnerabilities in a PPS can be isolated and fixed. The AOO should follow this process for each of the vulnerabilities and weaknesses they have discovered, and when complete, make an informed decision on the risks they face and the cost of meeting those risks.
To answer the question posed in the title, we see that prior to the upgrade, the site was vulnerable to an attack, but after the upgrade, the site would probably be successful in repelling it – at least for the scenario in the example.
About Ross Johnson
Ross Johnson has over four decades of experience in all aspects of security management, including tenures as a professional security manager where he oversaw regulatory requirements, budgets, personnel shortages and an endlessly expanding threat portfolio.. Having spent much of his career in the high-impact/low-frequency quadrant, he now assists organizations by developing programs that help them define the appropriate level of attention and resourcing that their risks need. Johnson has worked in the electric sector since 2006 and held executive committee positions on NERC and Electricity Canada’s security and infrastructure protection committees, including representing Canada on the CIP-014 Standards Drafting Team. He is currently the chair of E-ISAC’s Physical Security Advisory Group and co-facilitates the DBT/VISA workshop for NERC’s E-ISAC. Reach him at ross@bridgeheadsecurity.com.