Tag: Featured
Rocking the Boat: Why Challenging the Status Quo is Essential for Protection
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Facilities Security, Infrastructure Security, Cybersecurity.
Critical Infrastructure at a Crossroads: Cybersecurity Gaps in the Utility Sector
Written by Stacy Mill on . Posted in Cybersecurity.
Addressing Utility Fragility in the Face of Escalating Climate Disasters
Written by David Zelenok, P.E. on . Posted in Facilities Security.
Leadership Lessons and Strategies I Learned From PBS
Written by Shane Mark on . Posted in C-Suite Perspective.
The Myth of Delegated Security
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Frontline Worker Security.
Physical-Cyber Convergence is the Future of Utility Security
Written by Steve Sinclair on . Posted in Facilities Security, Cybersecurity.
Our Electricity Infrastructure: Built for a World That No Longer Exists
Written by Ross Johnson, CPP on . Posted in Infrastructure Security.
Will Your Critical Substation Survive an Attack? (Part Four)
Written by Ross Johnson, CPP on . Posted in Infrastructure Security.
LiDAR & 3D Modeling: A Pathway to Smarter & More Precise Utility Security
Written by webmaster on . Posted in Utility Security Update.
Crossed Wires: The GRC Gap Threatening Critical Infrastructure
Written by Brian Harrell on . Posted in Infrastructure Security, Cybersecurity, Facilities Security.
Substation Intrusion: Are You Ready To Response?
Written by Ross Johnson, CPP on . Posted in Infrastructure Security.
Worlds Colliding: Why Physical and Cybersecurity Convergence Is Critical for Utility Protection
Written by Joey St Jacque on . Posted in Infrastructure Security.
Beyond the Meter: Cyber Mandates Reshape the Future of Utility Security
Written by Stacy Mill on . Posted in Cybersecurity.
Key Strategies for Successful Security Meetings
Written by webmaster on . Posted in C-Suite Perspective.
5 Questions with Joe Weiss
Written by webmaster on . Posted in 5 Questions with a Utility Security Professional.
The Stalking, Swatting & Doxing Threat: How a Proactive Employee Protection Strategy is Key
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Frontline Worker Security.
The Ones and Zeros Have Taken Over
Written by webmaster on . Posted in Editorial.
Every Incident Tells a Story—Are You Listening?
Written by Haley Luis on . Posted in Infrastructure Security, Utility Security Update.
Utility Security: The Missing Link in Operational Competency
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in C-Suite Perspective, Utility Security Update.
Drone Technology is Evolving Rapidly: Can Detection & Mitigation Solutions Keep Up?
Written by William Edwards on . Posted in Utility Security Update.
7 Key Strategies for Better Disaster Response Security
Written by Ross Falisi on . Posted in Uncategorized.
New Research from AXIS Communications Reveals Video Surveillance AI Perspectives
Written by webmaster on . Posted in Utility Security Update.
Helping Secure Tomorrow Today: The SIA Utilities Advisory Board’s Aims to Educate the Next Generation of Utility Security Leaders
Written by Joey St Jacque on . Posted in Utility Security Update.
Theft, Ballistic Threats & Explosives, Oh My!
Written by webmaster on . Posted in Industry Events.
Beyond Security: How Thermal Camera Technology Is Being Used to Monitor Critical Utility Components
Written by webmaster on . Posted in Industry Events.
Convergint and Deloitte Partner to Build Holistic Utility Security Solutions
Written by webmaster on . Posted in Industry Events.
Building the Bridge Between Physical and Information Technology
Written by webmaster on . Posted in Utility Security Update.
‘Data Is the New Oil’: Talking Utility Security With Axis Communications’ Scott Dunn and Convergint’s Steve Sinclair
Written by webmaster on . Posted in Industry Events.
Upcoming Chicago Symposium Offers Utility Security Professionals Key IT-OT Security Strategies & Insights
Written by webmaster on . Posted in Industry Events.
FROM THE GROUND UP TO NEW HEIGHTS: Talking Cloud-Based Physical Security Strategies & Solutions with Sonoma County Water Agency’s Corey Jahn
Written by webmaster on . Posted in Utility Security Update.
Go West: ISC West 2025 Preview
Written by webmaster on . Posted in Industry Events.
Five Questions with ALCEA North America’s Managing Director Jerry Burns
Written by Jerry Burhans on . Posted in 5 Questions with a Utility Security Professional.
Sign of the Times: Using Federal Law to Help Deter Substation Attacks
Written by Ross Johnson, CPP on . Posted in Infrastructure Security.
Plan Your Path to Security Success: How Strategic, Tactical & Operational Planning are Essential to Creating a Strong Security Posture
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Infrastructure Security.
Will Your Critical Substation Survive an Attack (Part Two)
Written by Ross Johnson, CPP on . Posted in Infrastructure Security.
Securing Utility OT Networks: Best Practices and Strategies
Written by Stacy Mill on . Posted in Cybersecurity.
Facilities Security Requires a Comprehensive Approach
Written by Rene Rieder Jr on . Posted in Facilities Security.
Lessons Learned from the Brian Thompson Assassination
Written by Ross Falisi on . Posted in C-Suite Perspective.
If You’re in the Utility Business, You’re in the Security Business
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Frontline Worker Security.
Facilities Security Requires a Comprehensive Approach (Full Unedited Interview)
Written by webmaster on . Posted in Facilities Security.
Power Up: Using AI to Boost Utility Security and Resiliency
Written by Dave Gustafson on . Posted in Utility Security Update.
Vegas Lights, Utility Security Sights: ISC West 2025 Preview
Written by webmaster on . Posted in Industry Events.
How Unified Physical Security Solutions are Helping Utilities
Written by Thomasina Martin on . Posted in Cybersecurity.
The Real Bottom-Line Costs of False Alarms
Written by Yaron Zussman on . Posted in C-Suite Perspective.
Why Utility Cyberattack Risks Continue to Rise
Written by Shankar Somasundaram on . Posted in Cybersecurity.
Five Questions with Utility Technology Association President Vicky Wilson Turner
Written by webmaster on . Posted in 5 Questions with a Utility Security Professional.
ISC East Offers Utility Security Professionals a Wide-Range of Industry Specific Education & Resources
Written by Ronald L. Hawkins on . Posted in Facilities Security.
The Four Crucial Employee Security Skill Sets
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Frontline Worker Security.
Will Your Critical Substation Survive an Attack?
Written by Ross Johnson, CPP on . Posted in Infrastructure Security.
Reducing Copper Theft in the Electrical Sector: A Strategic Approach
Written by Ross Johnson, CPP on . Posted in Facilities Security.
Substation Security Challenges: Conducting Threat Assessments
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Facilities Security.
Danger from Above: The Time is Now to Address Drone Risks
Written by William Edwards on . Posted in Infrastructure Security.
Mastering the three “Cs” of Security: Clarity, Communication and Consistency
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Infrastructure Security.
5 Questions with Utility Security Expert & Author Ross Johnson
Written by webmaster on . Posted in 5 Questions with a Utility Security Professional.
Knowing Your Risks and Vulnerabilities and How to Prioritize Budget to Close Gaps
Written by Shawn Wallace and Glenn Engel on . Posted in C-Suite Perspective.
Secure by Design
Written by Sherri Middleton on . Posted in Cybersecurity.
Getting Smart with Padlocks
Written by Jerry Burhans on . Posted in Facilities Security.
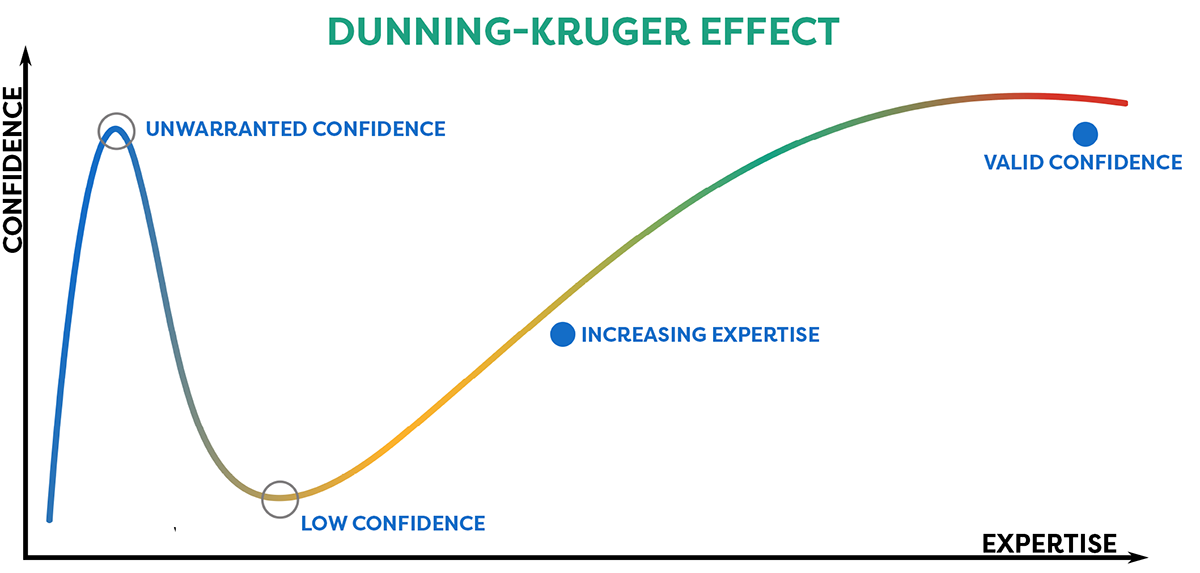
Do You Know What You Don’t Know? How to Overcome the Dunning-Kruger Effect and Expand Your Security Expertise
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Frontline Worker Security.
The AI Push to Smart and Speedy Security
Written by Jon Carstensen on . Posted in Infrastructure Security.
Regulation Turmoil Ahead?
Written by webmaster on . Posted in Cybersecurity.
Green Protection: Two Perspectives on How to Effectively Plan and Implement a Security Strategy for Renewable Energy Sources
Written by webmaster on . Posted in Infrastructure Security.
Homeland Security Conference Provides Attendees with New Insights to Threats
Written by webmaster on . Posted in Industry Events.
Protecting Water Utilities from Drone Threats: Understanding the Steps of a Drone Security Methodology that Support the J100 framework
Written by William Edwards on . Posted in Infrastructure Security.
Know Your Diamonds from Your Pencils: Talking All Things Physical Security with SERC’s Travis Moran
Written by webmaster on . Posted in Infrastructure Security.
Substation Security Challenges: The Importance of the Critical Decision Making Process
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Infrastructure Security.
Forging a Secure Tomorrow: Duke Energy’s Path to a More Resilient Future
Written by webmaster on . Posted in Infrastructure Security.
How ‘Global Weirding’ is Creating New Threats for Utility Security Professionals
Written by webmaster on . Posted in Infrastructure Security.
The Storm Work Security Conundrum
Written by webmaster on . Posted in Frontline Worker Security.
Perimeter Control as the First Line of Defense
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Facilities Security.
GridEx VII Reveals Continuing Challenges of Post-Covid Hybrid Work, Communications and Technology
Written by webmaster on . Posted in Cybersecurity.
Why Your Organization Needs to Conduct Exercises: Understanding the The Bottom-Line Impacts
Written by webmaster on . Posted in C-Suite Perspective.
5 QUESTIONS WITH ELECTRICAL & COMPUTER ENGINEERING RESEARCHER AND EDUCATOR CHEE-WOOI TEN
Written by webmaster on . Posted in 5 Questions with a Utility Security Professional.
Security LeadHER Event by SIA & ASIS International Provides Informative Career Growth & Personal Growth Insights to Female Leaders in the Security Industry
Written by UBM Staff on . Posted in Industry Events.
Key Situational Awareness & Response Strategies Your Frontline Workers Need to Stay Secure
Written by Charles Keeling, CUSP on . Posted in Frontline Worker Security, Utility Security Update.
How to Protect Utility Customers from Scams: A Conversation with Utilities United Against Scams Executive Director Michelle Martinez
Written by webmaster on . Posted in Cybersecurity, Utility Security Update.
Partnering with Law Enforcement to Improve Bomb Threat Prevention and Response: A Conversation with the Office for Bomb Prevention’s Charles Leas
Written by webmaster on . Posted in Facilities Security, Infrastructure Security, Utility Security Update.
Rethinking Utility Security for Field Workers
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Frontline Worker Security, Utility Security Update.
11 Key Questions to Ask Before You Plan Your Security Solution
Written by Darin Dillon on . Posted in C-Suite Perspective, Utility Security Update.
Driven to Protect
Written by webmaster on . Posted in Cybersecurity.
Threats on the Horizon: The Challenges of Securing the Nation’s Water Utilities and the Strategies to Overcome Them
Written by webmaster on . Posted in Infrastructure Security.
Are Assumptions Compromising Your Substation Security?
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Facilities Security.
The Emerging Cybersecurity Threats and Solutions of Artificial Intelligence (And Some Resources to Help Ready You for Both)
Written by webmaster on . Posted in Cybersecurity.
Are You Prepared for the Next Attack?
Written by Darin Dillon on . Posted in C-Suite Perspective.
5 Questions with Bomb Threat Expert Sean Haglund
Written by webmaster on . Posted in 5 Questions with a Utility Security Professional.
Are You Ready for a Drone Attack on Your Infrastructure?
Written by webmaster on . Posted in Infrastructure Security.
The Safety and Security Paradox
Written by Jim Willis, M.Sc, CMAS, CHS-V on . Posted in Frontline Worker Security.
From the Battle of Fallujah to Helping Utilities Respond to Active Shooter Incidents
Written by webmaster on . Posted in Facilities Security.